The State of Modern Authentication and Authorization
Lead Context
Authentication and authorization have become the primary bottleneck in distributed systems, yet engineering teams continue to treat them as solved problems. The prevailing architecture—stateless JWT tokens, OAuth 2.0 flows, and centralized identity providers—was designed for monolithic applications and modest user bases. Today’s microservices architectures, serverless deployments, and AI agent ecosystems expose fundamental constraints that most teams discover only after production failures. The real engineering problem is not choosing between JWT and sessions, but designing systems where identity verification scales sublinearly with request volume while maintaining security guarantees under partial failure.
The Hidden Assumption
The industry operates under a critical assumption: that stateless authentication eliminates scalability constraints. This assumption is breaking. Stateless JWTs were supposed to remove database lookups, yet teams now implement distributed revocation lists that reintroduce state. OAuth 2.0 was supposed to standardize delegation, yet its optional security features created vulnerability classes that OAuth 2.1 had to retroactively eliminate. API gateways were supposed to centralize authentication logic, yet they have become single points of failure that mask downstream authorization complexity. The assumption that identity can be both decentralized (for performance) and centrally controlled (for security) has produced architectures that achieve neither.
What’s Actually New
Four shifts define the current authentication landscape:
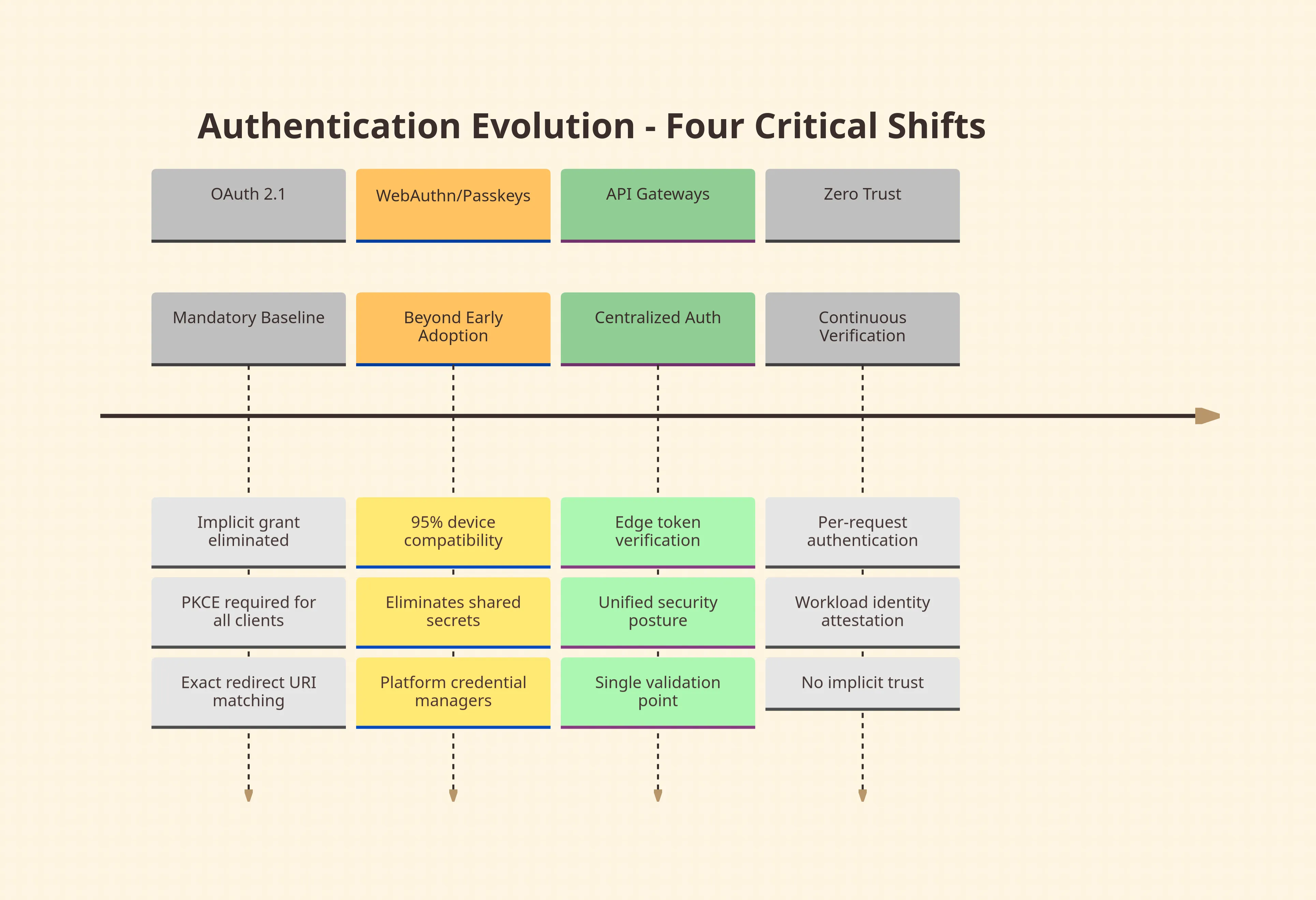
OAuth 2.1 as a mandatory baseline. The specification removes the implicit grant flow entirely, eliminates password credentials, and mandates PKCE for all clients. Exact redirect URI matching replaces flexible patterns. These are not incremental improvements but acknowledgments that optional security features created exploitable attack surfaces.
WebAuthn and passkeys moving beyond early adoption. With 95% device compatibility, the standard eliminates shared secrets but introduces new operational challenges: cross-device synchronization, account recovery without passwords, and reliance on platform-specific credential managers.
API gateway authentication becoming a default architectural pattern. Rather than distributing validation logic across services, teams now centralize token verification at the edge. This reverses the microservices ethos of decentralized logic but acknowledges that duplicated validation code produces inconsistent security postures.
Zero trust principles redefining authorization boundaries. Authentication is no longer a one-time event at login. Every service-to-service call requires continuous verification, moving from network perimeter trust to workload identity attestation based on runtime environment proofs.
Technical Deep Dive
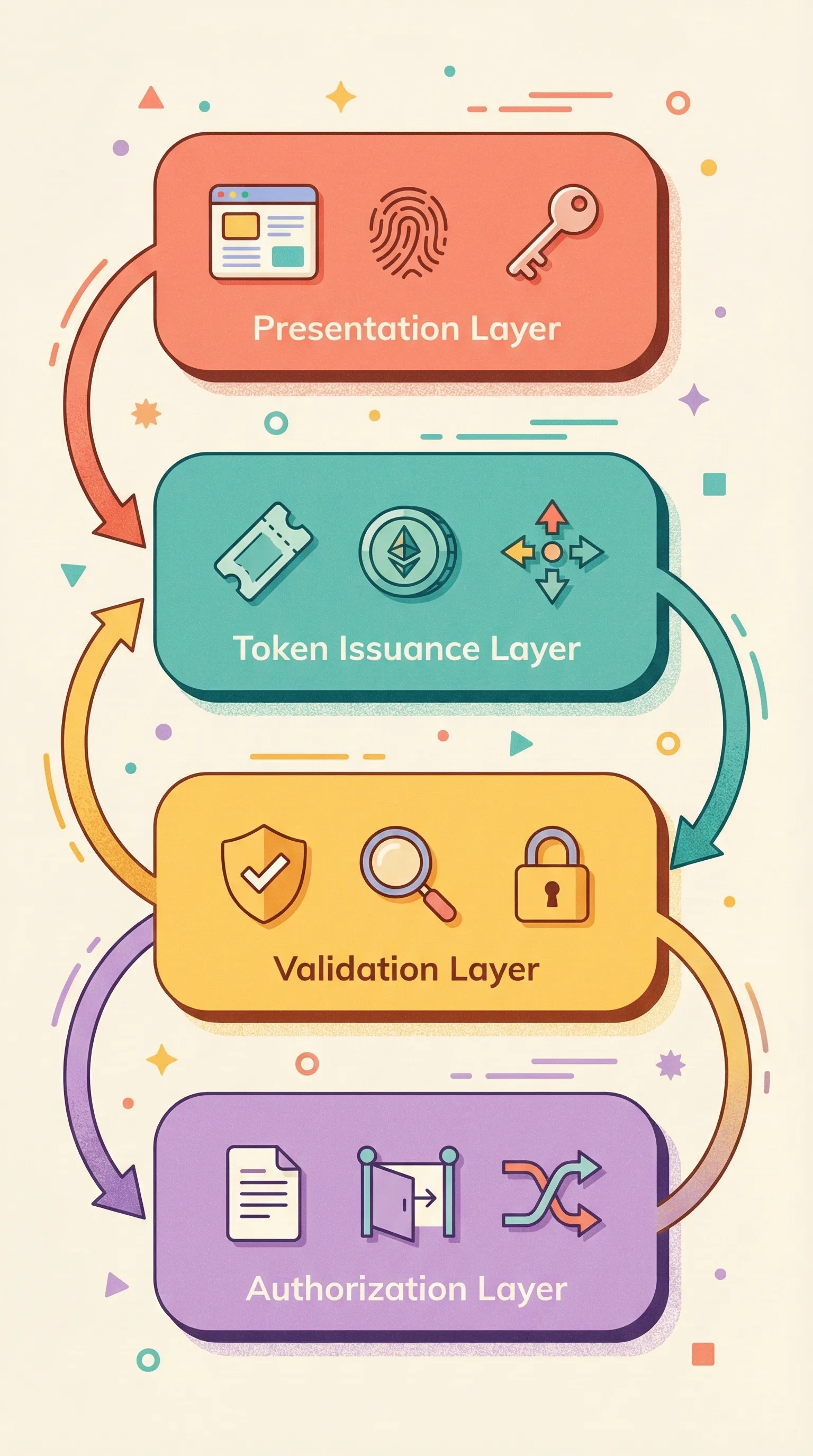
System Components
Modern authentication systems decompose into four layers:
- Presentation Layer: Handles credential collection. For WebAuthn, this involves generating challenge nonces and validating attestation statements. For OAuth 2.1, this means authorization endpoints and PKCE parameter generation.
- Token Issuance Layer: The authorization server issues access tokens, refresh tokens, and ID tokens. OAuth 2.1 requires refresh token rotation: each refresh invalidates the previous token and issues a new pair. This prevents replay attacks but introduces state that must be stored atomically to avoid race conditions.
- Validation Layer: API gateways validate JWT signatures using JWKS endpoints. Validation includes issuer, audience, expiration, and signature checks. Asymmetric signing (RS256, ES256) is now standard to prevent signature key compromise from enabling token forgery.
- Authorization Layer: Microservices perform fine-grained access control based on claims embedded in tokens or through policy engines like OPA. This layer must handle token propagation across service boundaries and implement defense-in-depth when the gateway validation fails.
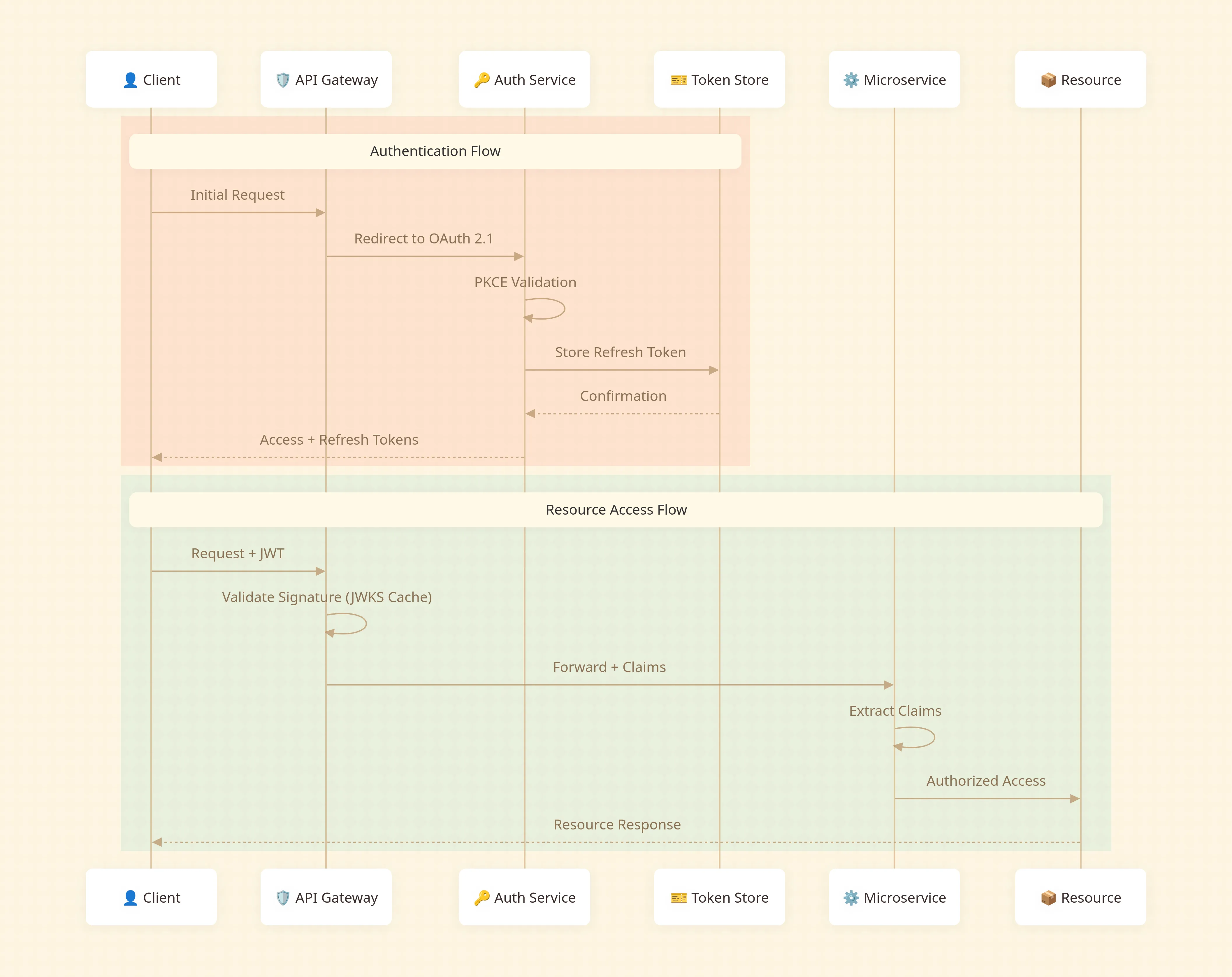
Data Flow
A request traverses the system as follows:
Client → API Gateway → Auth Service (OAuth 2.1) → Token Issuance → Client
Client → API Gateway (JWT Validation) → Microservice (Claims Extraction) → Resource AccessThe gateway caches JWKS responses with strict TTLs to avoid hammering the authorization server. Microservices must defend against cached key staleness by implementing circuit breakers that fall back to direct JWKS fetching during key rotation events.
Compute Model
Authentication transforms from stateless to eventually-consistent stateful. Refresh token rotation requires durable storage with atomic compare-and-swap semantics. Redis with Lua scripts is common, but this introduces a single point of failure that contradicts the stateless premise. Distributed consensus systems like etcd or Consul are emerging for token revocation lists, adding 10-20ms latency per validation.
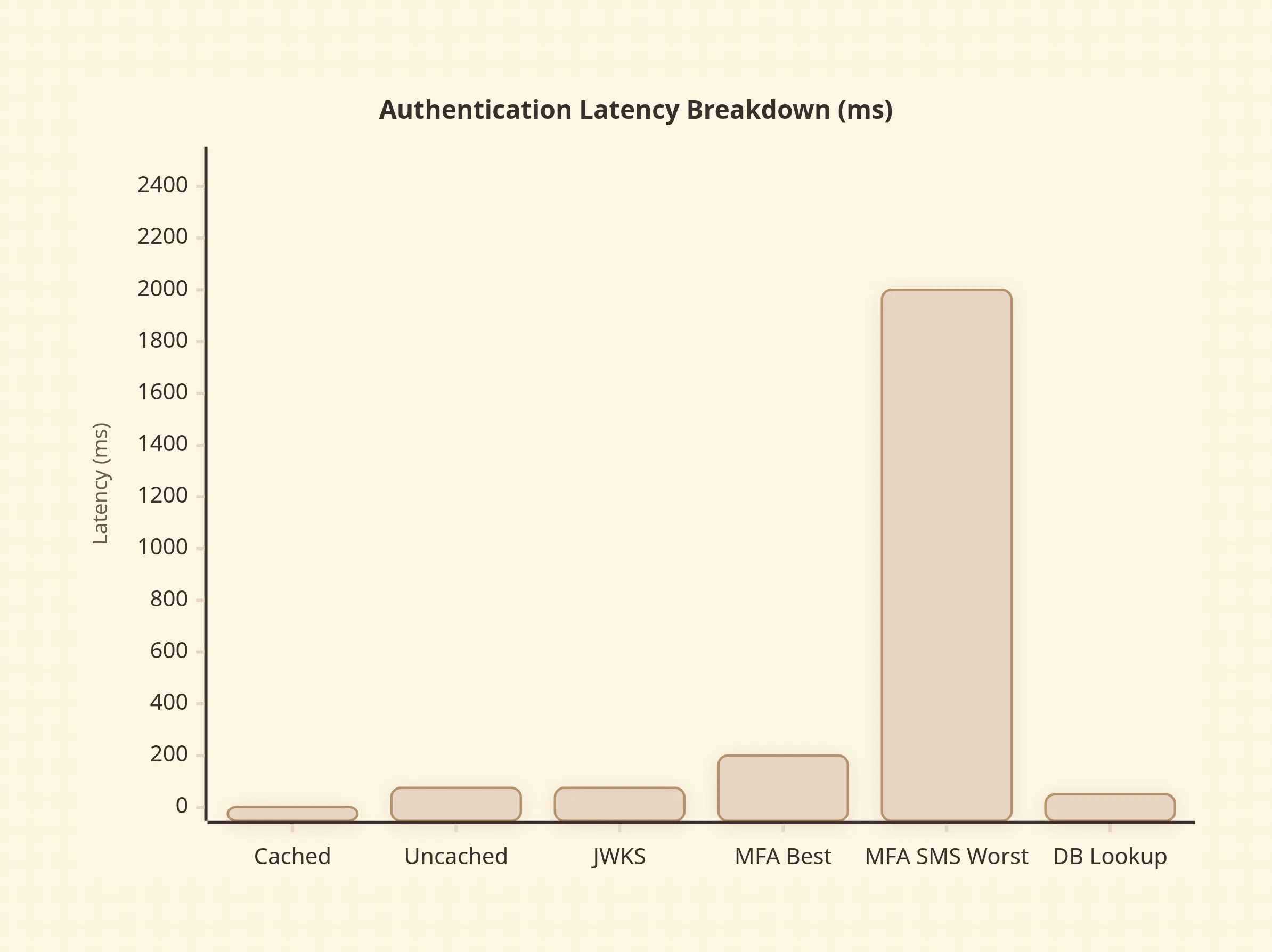
Performance Characteristics
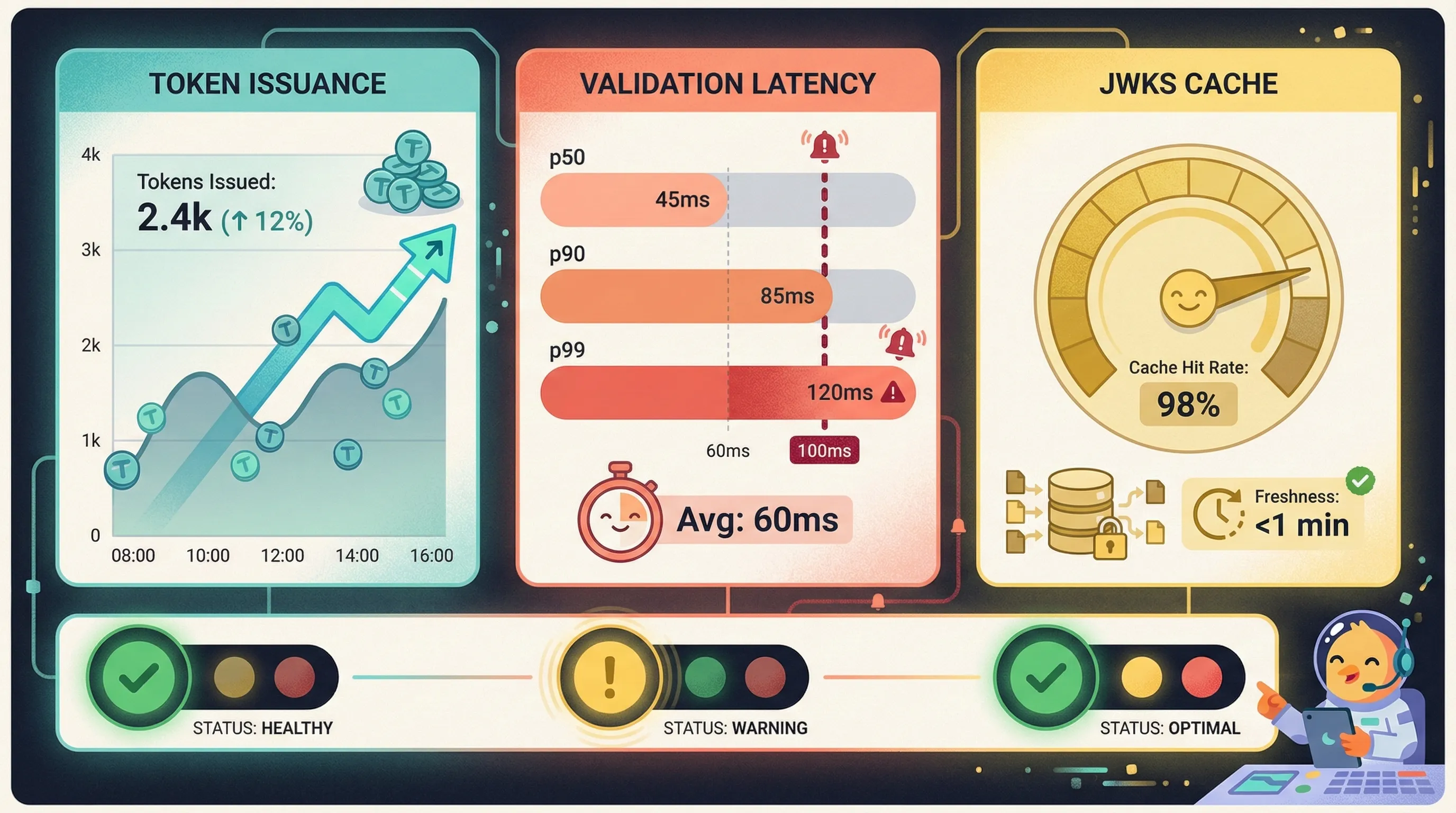
Token validation at the gateway adds 1-3ms per request with local caching. Without caching, JWKS fetching adds 50-100ms and creates a thundering herd problem during key rotation. Third-party MFA providers introduce 200-500ms variance; SMS delivery can exceed 2 seconds. Authentication bottlenecks during peak traffic often stem from database queries for refresh token validation, not signature verification.
Security Implications
Algorithm confusion attacks (CVE-2023-48238, CVE-2024-54150) demonstrate that JWT libraries trusting the alg header enable signature bypass. OAuth 2.1’s exact redirect URI matching prevents open redirects, but misconfigured callback URLs remain a top vulnerability. Passkeys eliminate credential theft but create account recovery gaps when users lose all devices. The lack of native backup mechanisms forces teams to implement weaker recovery flows that become the new attack vector.
Where It Fails
Constraints
- Token size: JWTs with extensive claims exceed 4KB, causing HTTP header overflow and forcing compression or alternative transmission methods.
- Key rotation: Rotating signing keys without breaking in-flight requests requires overlap periods that most libraries poorly support, causing signature validation failures during deployment windows.
- Revocation latency: Distributed revocation lists propagate with eventual consistency measured in seconds, allowing token reuse during that window after logout or breach detection.
Bottlenecks
- Authorization server: During peak load, token issuance becomes CPU-bound due to cryptographic operations. Horizontal scaling is limited by refresh token storage requirements that must be strongly consistent.
- Third-party MFA APIs: Rate limits from providers like Twilio or Google Authenticator create hard ceilings on login throughput. Circuit breakers trigger prematurely under normal load variance.
- Database queries: Refresh token validation queries against PostgreSQL or MySQL linearly degrade with table size, even with indexing. Teams often implement separate Redis caches that introduce cache coherence issues.
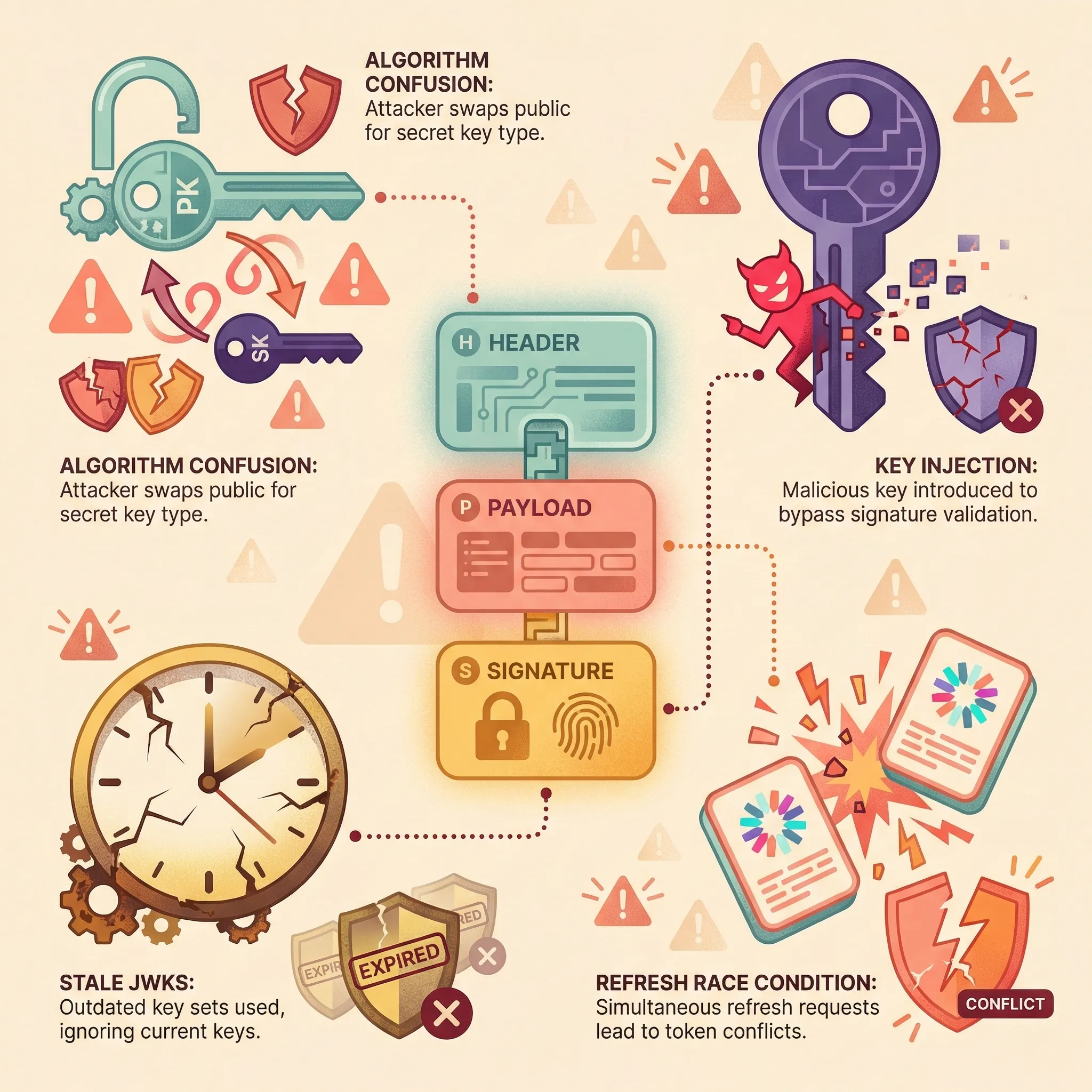
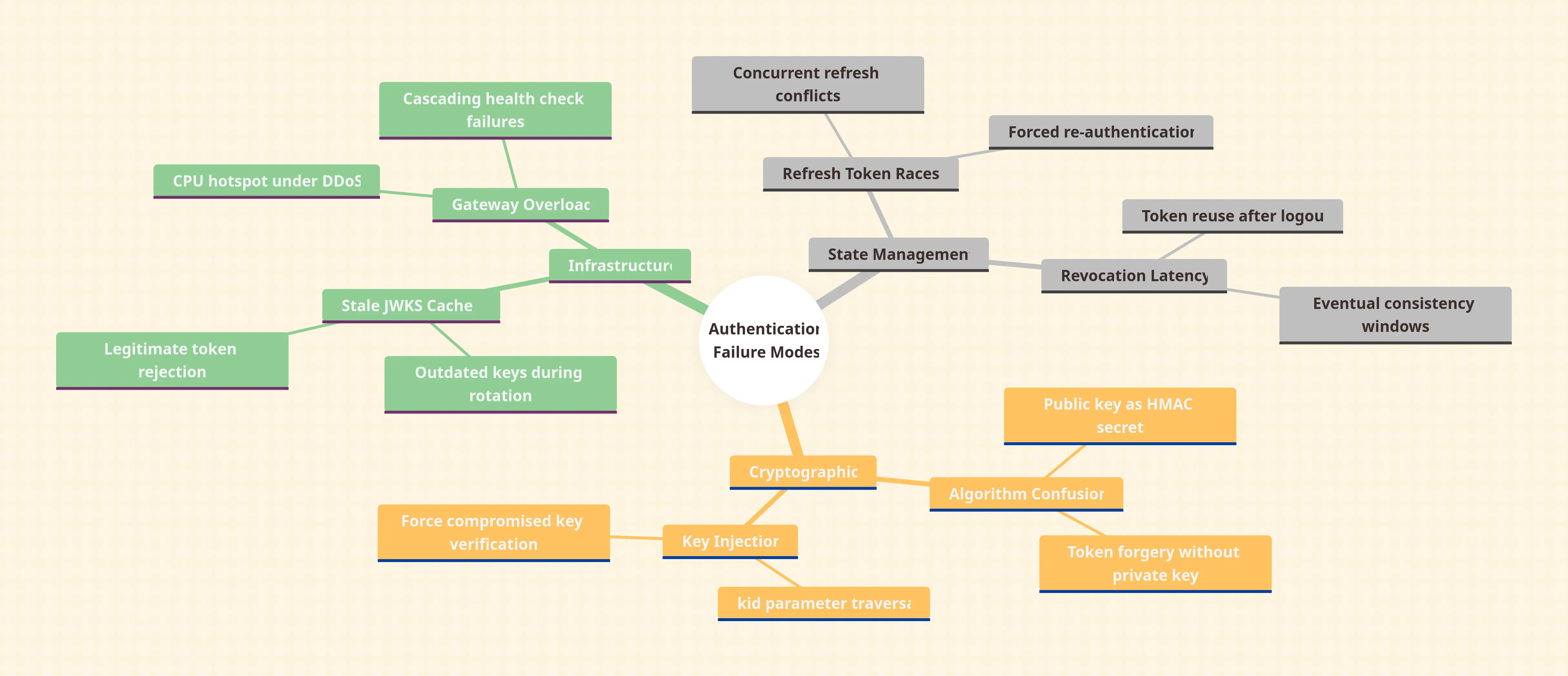
Failure Modes
- Algorithm confusion: Public key used as HMAC secret forges tokens without private key access.
- Key injection:
kidparameter traversal (CVE-2024-…) allows attackers to force verification with compromised keys. - Stale JWKS: Gateway caches outdated keys during rotation, rejecting legitimate tokens until cache expiry.
- Refresh token race conditions: Concurrent refresh requests with rotation enabled can invalidate valid tokens, forcing user re-authentication.
- API gateway overload: Gateway authentication filters become CPU hotspots under DDoS, blocking health checks and causing cascading failures.
Compatibility Issues
OAuth 2.1 eliminates flows that legacy mobile apps depend on. SPAs using implicit grants require complete rewrites to use authorization code flow with PKCE. Passkey implementations break on older Android versions that lack proper WebAuthn support, requiring fallback to less secure methods.
Impact on Business & Engineering Teams
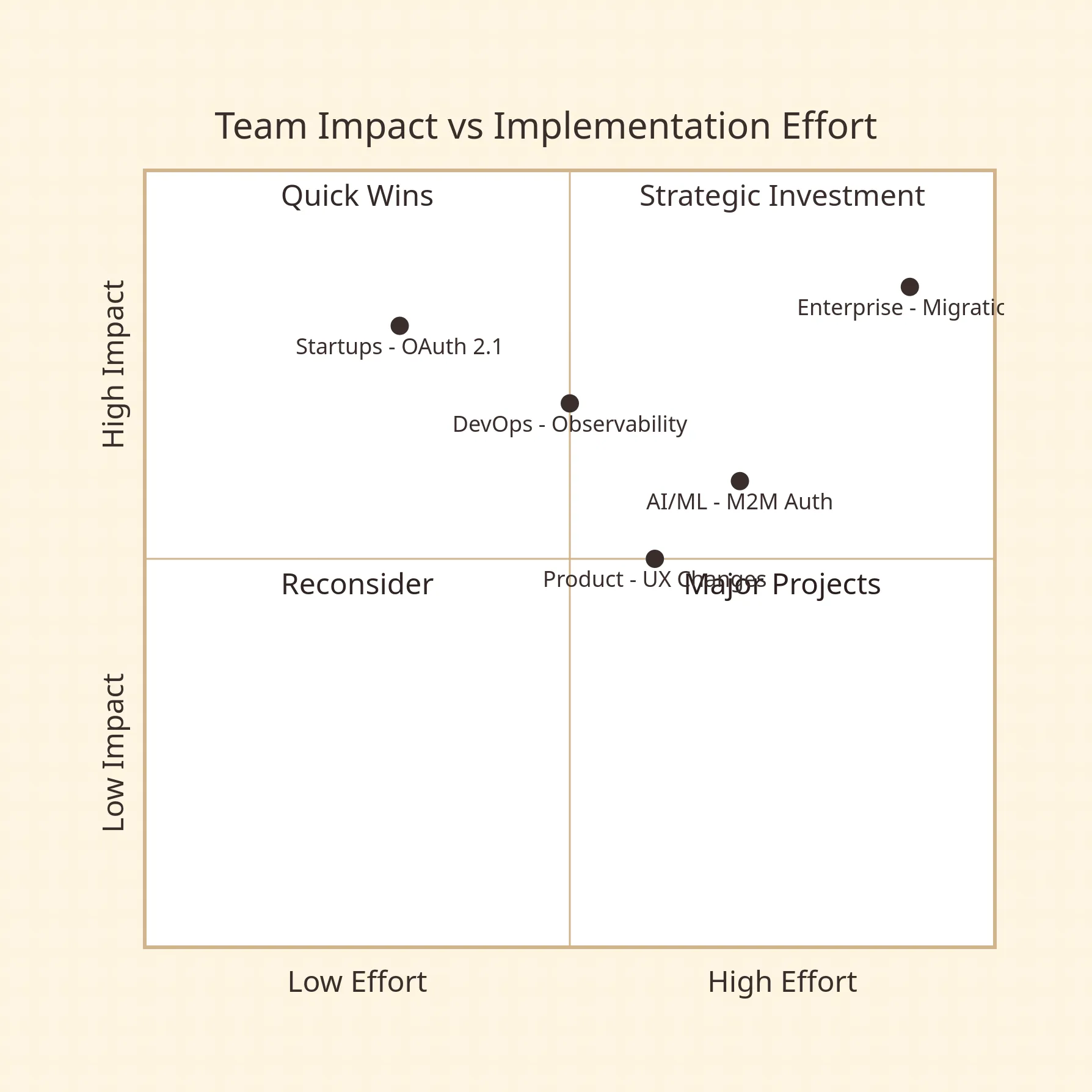
Startups
Focus on OAuth 2.1 from day one. Avoid JWT libraries older than 2023; they likely have algorithm confusion vulnerabilities. Use managed identity providers (Auth0, Cognito) initially, but model token revocation logic from the start—migrating later is costly. For passkeys, wait until 2025 Q2 when cross-platform sync stabilizes. Current implementations will require substantial rework as platform behavior changes.

Enterprise Engineering Teams
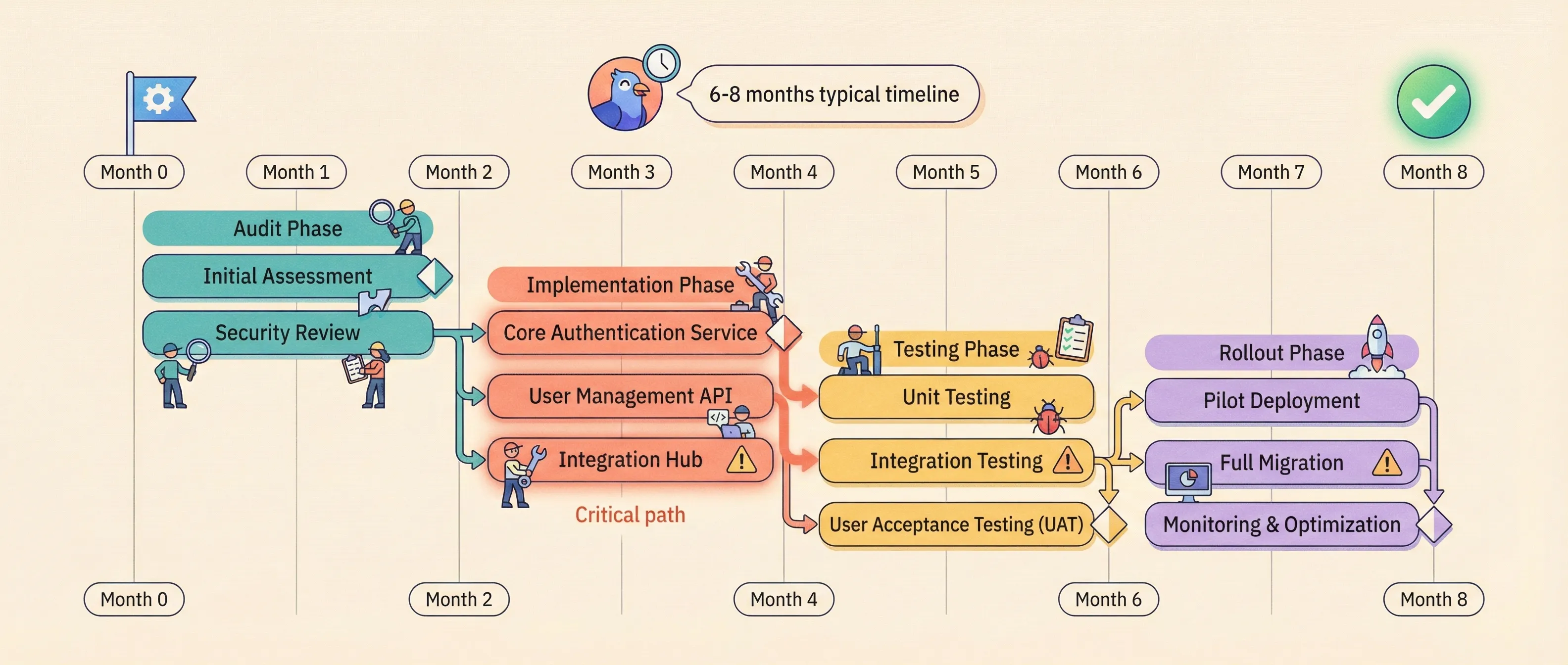
The shift to OAuth 2.1 requires auditing every redirect URI and implementing exact matching across hundreds of registered applications. Expect 6-8 month migrations for large codebases. Refresh token rotation demands atomic database operations; most existing authorization servers lack this, requiring custom logic. API gateway centralization means retraining platform teams on edge authentication and debugging token validation failures that previously appeared in application logs.
DevOps Teams
Authentication observability must cover three dimensions: token issuance metrics, validation latency percentiles, and JWKS cache hit rates. Deploy JWKS rotation during low-traffic windows with circuit breakers configured to bypass cache if error rates spike. For passkeys, implement attestation logging to detect anomalous authenticators. Monitor third-party MFA latency with SLOs that trigger automatic fallback to backup codes.
Product Teams
OAuth 2.1 eliminates password grants, forcing UX changes where users previously entered credentials directly. Account recovery flows for passkey-only accounts require new designs that balance security with usability. Expect 15-20% increase in support tickets during migration as users encounter new authentication patterns.
AI/ML Teams
Machine-to-machine authentication remains a gap. OAuth 2.1’s client credentials flow still uses static secrets, creating credential management overhead for ephemeral training jobs. Consider SPIFFE/SPIRE for workload identity or vendor-specific solutions like AWS IAM Roles for Service Accounts. JWT validation overhead adds 2-3ms per intra-service call, which compounds for model serving pipelines with dozens of microservices.
Recommended Actions
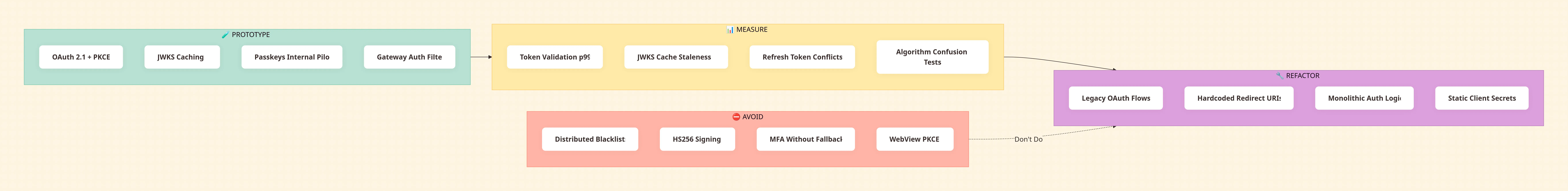
What to Prototype
- OAuth 2.1 with PKCE: Implement proof-of-concept using authorization code flow for your highest-traffic SPA. Measure latency impact of PKCE parameter generation.
- JWKS caching strategies: Test Redis vs. in-memory cache hit rates during key rotation events. Use consistent hashing to distribute cache keys.
- Passkeys with cross-device sync: Pilot with internal users on iCloud Keychain and Google Password Manager. Document recovery flows when users lose devices.
- API gateway authentication filter: Benchmark throughput degradation with and without token validation at the gateway. Profile CPU usage under synthetic load.
What to Avoid
- Do not implement JWT revocation as a distributed blacklist without considering consistency models. Eventual consistency creates security windows.
- Avoid using HS256 for signing. Asymmetric signing is now table stakes; secret key compromise is catastrophic.
- Do not rely on third-party MFA APIs without circuit breakers and explicit fallback mechanisms. Their downtime becomes your downtime.
- Skip the OAuth 2.1 migration if your application uses embedded browsers or WebViews; PKCE support is inconsistent across platforms.
What to Measure
- Token validation p99 latency: Track at gateway and microservice layers separately. Alert on divergence.
- JWKS cache staleness: Measure time between key rotation and cache update across all gateways. Target
<5 seconds. - Refresh token rotation conflicts: Log compare-and-swap failures. If
>0.1% of refreshes conflict, your atomic operations are insufficient. - Algorithm confusion test coverage: Your JWT library tests must explicitly verify rejection of mismatched
algheaders.
What to Refactor
- Legacy OAuth 2.0 flows: Eliminate implicit grant and password credentials. Budget 2-3 weeks per application.
- Hardcoded redirect URIs: Move to configuration-as-code with exact string matching enforced by CI/CD validation.
- Monolithic authorization logic: Decompose into gateway validation (authentication) and service-level policy engines (authorization).
- Static client secrets: Migrate to dynamic client registration with rotated secrets or workload attestation for machine-to-machine flows.
What Skills Are Required
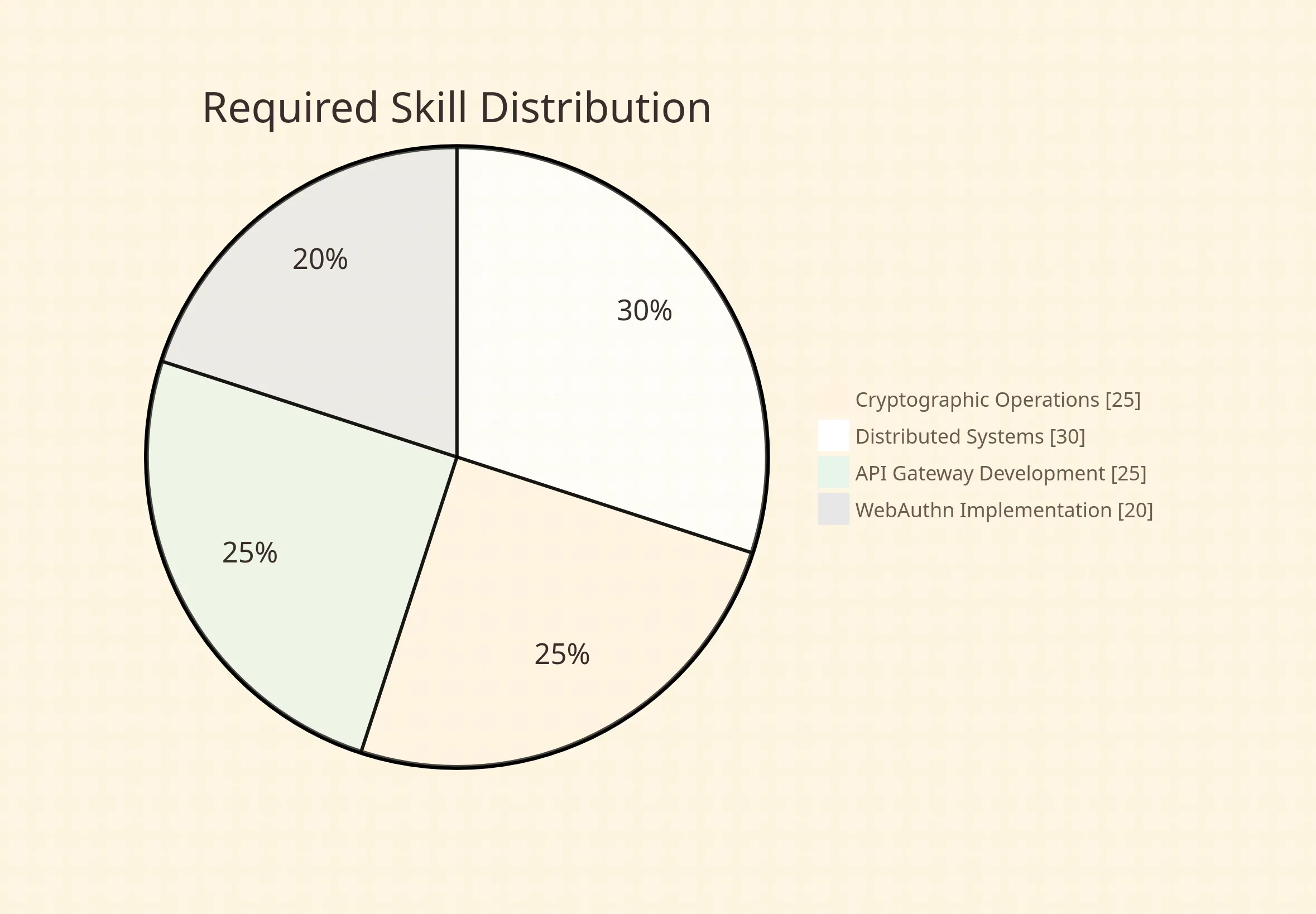
- Cryptographic operations profiling: Engineers must understand RSA/ECDSA verification overhead and key sizing tradeoffs.
- Distributed systems consistency models: Understanding of linearizable vs. eventual consistency for token revocation and refresh token rotation.
- API gateway plugin development: Custom authentication filters in Envoy or NGINX require C++/Lua expertise.
- WebAuthn attestation validation: Parsing and verifying attestation statements from multiple authenticator vendors.
The Aexaware Verdict
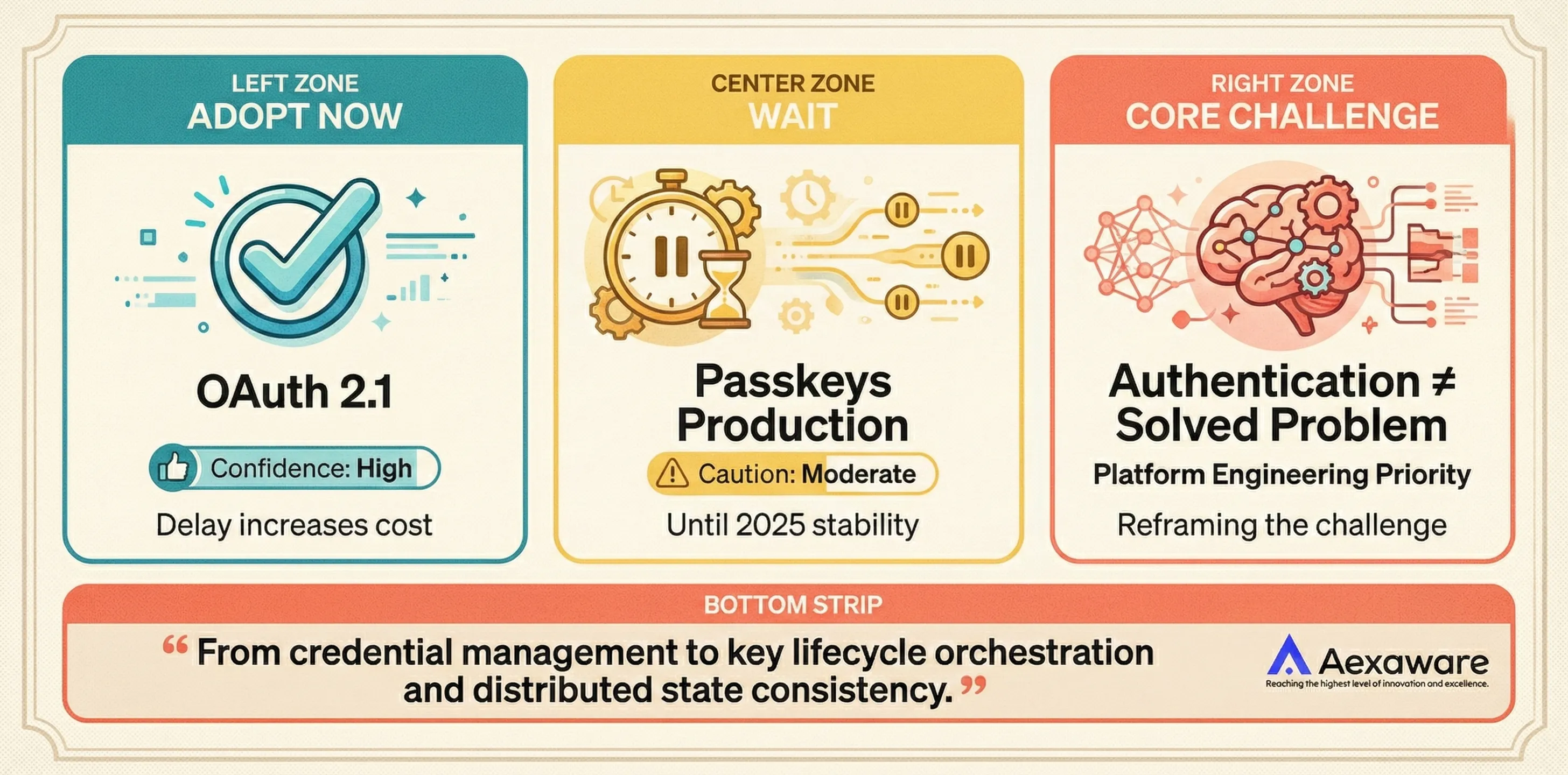
Modern authentication enables fine-grained, continuous verification across distributed systems but complicates operational simplicity. OAuth 2.1 eliminates entire vulnerability classes at the cost of breaking legacy integrations. Passkeys offer genuine passwordless security but create new account recovery challenges that remain unsolved at the protocol level. Teams should adopt OAuth 2.1 now—delaying only increases migration cost—but should wait on production passkey rollouts until cross-platform synchronization behavior stabilizes in 2025. The engineering overhead has shifted from credential management to key lifecycle orchestration and distributed state consistency, requiring skills that most teams must develop rather than hire for. Authentication is no longer a solved problem; it is now a core distributed systems challenge that belongs in the platform engineering roadmap, not as an afterthought in application logic.
Aexaware Technology Review provides grounded analysis for engineering teams building scalable digital systems. For implementation support across the Discovery → Development → Testing → Growth lifecycle, contact Aexaware Infotech.